ZCS Checklist-Driven Implementation Model
May 08, 2025 14:43 PM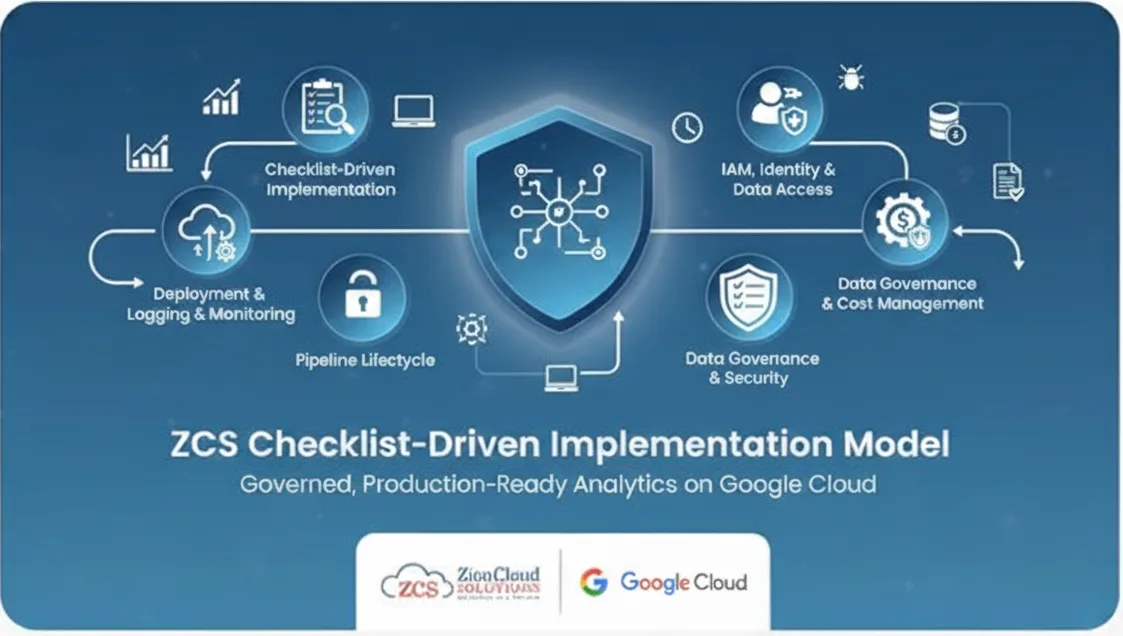
ZCS Checklist-Driven Implementation Model
How we deliver governed, production-ready analytics on Google Cloud
Most data projects fail not because of technology, but because the implementation is inconsistent: one team sets up IAM by hand, another forgets to enable logging, a third never documents how the pipeline actually runs. Zion Cloud Solutions (ZCS) solves this with a checklist-driven implementation model that standardizes how we build and operate data platforms on Google Cloud.
Instead of relying on tribal knowledge, we use a curated set of implementation checklists and runbooks that every project follows—from first project creation through long-term operations. These checklists are battle-tested across our government and commercial customers and are continuously updated in our internal Quality Management System.
Think of them as a “runbook blueprint” for your data platform.
- Deployment & Orchestration Checklist
Make every environment repeatable, not handcrafted
This checklist ensures that every environment—PoC, dev, test, or production—is created and configured the same way, using automation wherever possible.
What it covers
- Project & folder creation
- Standard naming conventions, folder placement, and linkage to the correct billing account.
- Baseline organization policies (CMEK requirement, public access prevention, allowed regions, etc.).
- Service enablement
- Required APIs for BigQuery, Cloud Storage, Dataflow, Cloud Data Fusion, Dataplex, Cloud Run, Vertex AI, Document AI, AlloyDB, Logging, and Monitoring.
- Explicit documentation of which services are used and why.
- Infrastructure as Code / CI/CD
- Scripts or templates (e.g., Terraform, bash, Cloud Build pipelines) for:
- Creating projects and networks.
- Deploying Cloud Functions/Cloud Run services.
- Registering Dataflow templates and Data Fusion instances.
- Version control and change tracking for all infrastructure changes.
- Orchestration patterns
- Standard patterns for:
- Scheduled jobs (Cloud Scheduler → Pub/Sub → Dataflow/Data Fusion).
- Event-driven ingestion (webhooks → Cloud Functions/Run → Cloud Storage).
- Batch vs near-real-time pipelines.
Why it matters for customers
- Environments can be re-created in hours, not weeks.
- No “snowflake” projects—every environment is auditable, reproducible, and ready for hand-over.
- Faster onboarding of new use cases because they plug into a known, proven deployment pattern.
- IAM, Identity & Data Access Checklist
Design security once, reuse it everywhere
Identity and access is where most cloud projects drift over time. Our IAM checklist forces consistency and least privilege from day one.
What it covers
- Role models & custom roles
- Standard role sets for:
- Data Engineers, Analytics Engineers, BI Developers.
- Platform/Cloud Engineers and Security Engineers.
- Data Governance and Data Quality owners.
- Custom roles that bundle only the permissions these personas need for:
- BigQuery, GCS, Dataflow, Cloud Run.
- Dataplex, Logging, Monitoring, KMS, Secret Manager.
- Service accounts
- Dedicated service accounts for:
- Ingestion (e.g., SharePoint/email connectors).
- ETL/ELT pipelines (Dataflow, Data Fusion).
- Application backends (Cloud Run, Functions).
- AI services (Vertex AI, Document AI calling patterns).
- Clear rules: no shared service accounts, no broad “Editor/Owner” bindings.
- Data-level access
- Dataset-level and table-level permissions in BigQuery.
- Column-level security using Dataplex policy tags for PII, financials, and other sensitive fields.
- Access patterns for AlloyDB or other OLTP stores with clear tenant isolation.
Why it matters for customers
- Security posture is consistent across teams and projects.
- Fast audits: we can show exactly which identities can do what, on which datasets and pipelines.
- Easy to adapt the same model when you add new data domains or agencies.
- Data Governance & Security Checklist
Governance is not an afterthought—it’s part of the pipeline
This checklist ensures that data is not just ingested, but governed—profiled, classified, and monitored throughout its lifecycle.
What it covers
- Data catalog & classification
- Registration of key datasets and tables in Dataplex.
- Assignment of domains (e.g., “Finance”, “Procurement”, “Case Management”).
- Tagging of sensitivity levels (Public, Internal, Confidential, Restricted).
- Data quality rules
- Definition of rules by table/column:
- Required fields and non-null checks.
- Value ranges (e.g., amount > 0, dates in valid windows).
- Referential integrity checks between tables.
- Uniqueness constraints (e.g., invoice_number must be unique per vendor).
- Scheduling of data quality scans and thresholds for alerts.
- Security controls
- Enforcement of CMEK for all buckets and critical datasets.
- Public access prevention on buckets and restricted external sharing.
- Optional Cloud DLP integration for pattern-based PII detection.
Why it matters for customers
- Data quality is visible and measurable (scores, passed/failed rules, trends).
- Governance is built into the platform, not bolted on at reporting time.
- Provides tangible proof for auditors and regulators that data is handled correctly.
- Pipeline Lifecycle Checklist
Every pipeline follows the same “Ingest → Store” pattern
Instead of treating each pipeline as a bespoke one-off, ZCS enforces a standard lifecycle. This makes it easy to understand, document, and extend pipelines over time.
Lifecycle stages
- Ingest
- Define where data comes from (SharePoint, email, SFTP, APIs, databases, user uploads).
- Decide whether ingestion is batch, micro-batch, or event-driven.
- Implement with the right tools:
- Cloud Data Fusion / Dataflow for structured sources.
- Cloud Functions/Run + Cloud Storage for file and document intake.
- Transform
- Apply cleansing, schema mapping, normalization, enrichment, and business rules.
- For AI/document use cases, call Document AI or Vertex AI to extract entities, embeddings, or summaries.
- Capture transformation logic in code, configs, or Beam pipelines—never as undocumented “magic” in a dashboard.
- Curate
- Separate raw, processed, and curated layers in BigQuery or other stores.
- Apply quality checks and promote only validated data to curated datasets.
- Ensure curated tables follow naming conventions, partitioning, and clustering best practices.
- Query & Explore
- Optimize for analysts and data scientists:
- Clear schemas and documentation.
- Sample queries and views.
- Sandbox spaces for ad-hoc exploration.
- Analyze & Visualize
- Connect BI tools (Power BI, Looker Studio, Looker) or custom portals to curated datasets.
- Standardize KPI definitions and metric calculation logic so every dashboard tells the same story.
- Store & Retain
- Define retention policies for raw (Cloud Storage) and curated (BigQuery) layers.
- Use lifecycle rules for automatic archiving and cost optimization.
- Document where the “system of analytical record” lives for each domain.
Why it matters for customers
- Every pipeline can be explained in one slide following the same pattern.
- Onboarding new teams is easier—they recognize the lifecycle from other projects.
- When something goes wrong, it’s clear which stage to inspect and what checks should have run.
- Billing, Tagging & Cost Management Checklist
Control cost from the start, not after the first surprise invoice
Cloud analytics can become expensive if cost governance isn’t designed in. This checklist keeps spend transparent and predictable.
What it covers
- Project & environment separation
- Dedicated projects per program or customer, with clear boundaries between dev, test, and prod.
- Ability to attribute cost by customer, agency, or line of business.
- Standard labels and tags
- Labels such as customer, environment, system, component, cost-center applied to:
- BigQuery datasets and jobs.
- GCS buckets.
- Dataflow and Dataplex resources.
- Cloud Run services and AI endpoints.
- Budgets & alerts
- Budgets configured per project or environment.
- Alerts when spend exceeds thresholds or when anomalies (e.g., a spike in query cost) are detected.
- Cost optimization patterns
- Guidelines for:
- BigQuery partitioning and clustering.
- Use of materialized views versus ad-hoc queries.
- Storage tier choices (standard vs long-term vs archival).
- Scheduling heavy jobs during off-peak hours.
Why it matters for customers
- Finance teams get clear cost attribution and no surprises.
- Technical teams get guardrails instead of retroactive cost policing.
- Proof that modernization leads to controlled spend, not runaway bills.
- Networking, Logging & Monitoring Checklist
Design for observability and secure connectivity
The final checklist ensures that every solution is observable and securely connected from day one.
What it covers
- Networking
- VPC design (subnets, regions, IP ranges) aligned to security and latency needs.
- Private access to Google APIs (Private Service Connect / Private Google Access) where required.
- Firewall rules and routing that support data pipelines without exposing unnecessary attack surface.
- Logging
- Enabling Cloud Logging for all core services (Dataflow, Cloud Run, Functions, BigQuery, Dataplex, AlloyDB).
- Defining a logging strategy:
- What is logged (errors, performance metrics, audit events).
- How logs are structured (correlation IDs, tenant identifiers).
- Retention policies and optional export to SIEM or log archives.
- Monitoring & alerting
- Dashboards for pipeline health (throughput, latency, error count).
- Alerts for:
- Failed jobs or ingestion runs.
- Degraded data quality scores.
- Resource saturation (CPU, memory, storage).
- Auditability
- Cloud Audit Logs enabled for admin and data access events.
- Playbooks for reviewing and responding to security or operational incidents.
Why it matters for customers
- Operations teams can see the health of their data platform at a glance.
- Security teams have visibility into who did what and when.
- Issues are caught early—before they affect downstream decision-making.
What This Model Delivers
By enforcing this checklist-driven implementation model across all projects, ZCS gives customers:
- Consistency – Every new use case benefits from the same battle-tested patterns.
- Speed with control – Rapid deployments without sacrificing governance or security.
- Audit-readiness – Clear artefacts that demonstrate how data is deployed, secured, monitored, and governed.
- Scalability – A foundation that can grow from a single PoC to a multi-agency, multi-domain data platform.
This is how ZCS turns Google Cloud into a repeatable data platform, not just a collection of services—and how we ensure that every analytics or AI project we deliver is ready for real-world use, not just a demo.
Related Blogs
Explore More
OneLake Intelligence: The New Operating System for Enterprise Data
Every organization today is drowning in storage accounts, warehouses, lakes, pipelines, and layers of integration work that nobody fully controls…
How Gemini Gets Its Enterprise Body and a Digital Bulletproof Vest
Stop the presses. We need to talk about the AI workflow you’re building right now. If you’re like most of…

What’s Next for Microsoft Fabric and the Modern Analytics Stack
Businesses today are drowning in data, yet insights often arrive too late to influence decisions. The modern analytics stack, once…

